On April 1, President Obama released an Executive Order titled “Blocking the Property of Certain Persons Engaging in Significant Malicious Cyber-Enabled Activities”. Cybersecurity has become a very important aspect of our country’s security, so at a glance this order seems like a good step towards keeping our nation’s critical infrastructure safe. But there are some important reasons why this might not be the case.
I spend a lot of time in the command line. Over time I have come across these valuable tools.
This semester I joined the Ramblin Rocket Club at Georgia Tech and last week I had a successful launch and recovery of my first rocket.
In my English 1102 class at GA Tech this summer, we were assigned a project: present on a topic of curiosity. While there were options to create a book or a website, my group decided to make an exhibit of physical objects. In keeping with the standards of museums, I thought I would create an audio device to accompany the visual exhibit. This would be a perfect use for my Raspberry Pi.
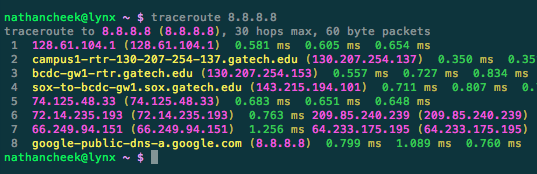
About 2 months ago, I checked our ISP’s website about getting a dual-stack connection. The website said that our area was covered, but after enabling IPV6, our router didn’t seem to be picking up an IPV6 address. When I called their customer support, they assured me that we were not actually in an area with coverage, even though their site said otherwise. I forgot about this whole debacle until today.